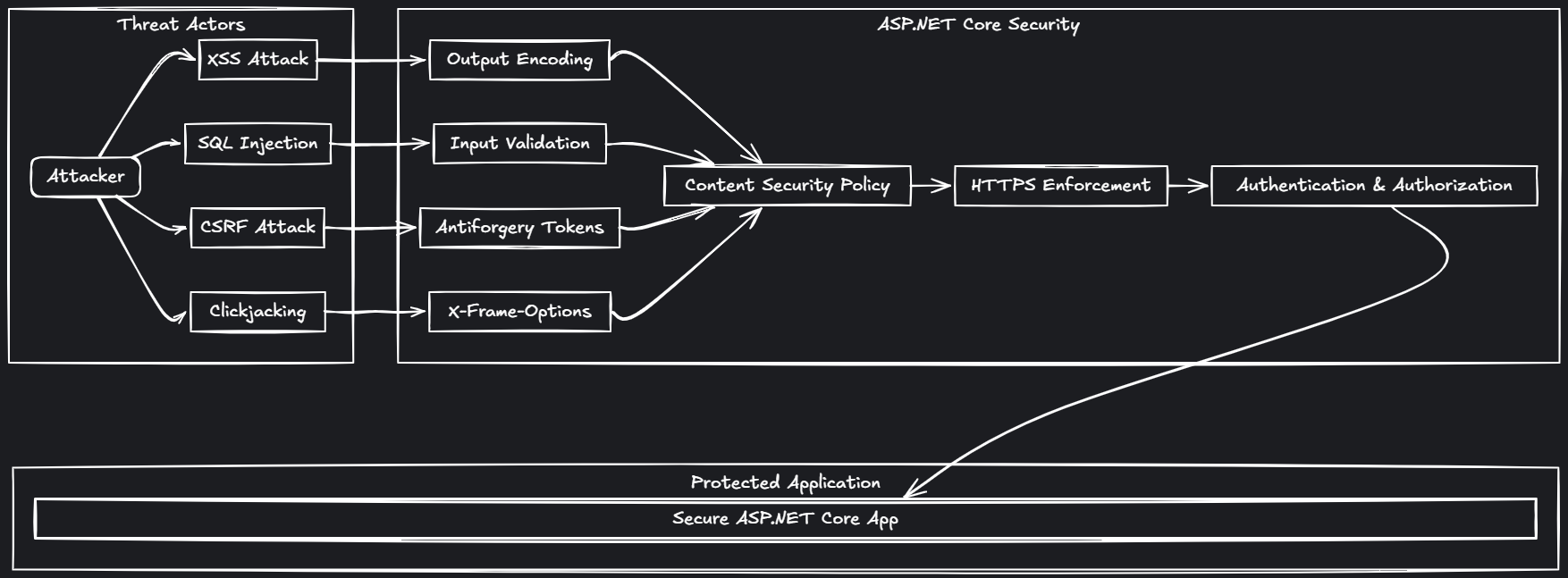
TL;DR: ASP.NET Core Security: Preventing Attacks Use input validation (Data Annotations, ModelState) to block XSS and SQL injection in ASP.NET Core. Always enable output encoding in Razor views and avoid using Html.Raw() with user input. Enforce HTTPS for all environments to protect data in transit. Implement authentication and authorization using [Authorize], roles, and policies. Protect against CSRF with antiforgery tokens and [ValidateAntiForgeryToken] attributes. Add security headers like Content-Security-Policy, X-Frame-Options, and Strict-Transport-Security. Store passwords securely using ASP.NET Core Identity or strong hashing algorithms. Use parameterized queries or ORMs to prevent SQL injection. Regularly update dependencies and monitor for new security threats. For API protection, use HTTPS, authentication, input validation, proper status codes, rate limiting, and versioning. ASP.NET Core is a modern web development framework that provides a variety of built-in security features to help prevent attacks on web application. Here are a few ways we can use ASP.NET Core to prevent attacks:
...